WPICTF - bogged
14 Apr 2019description: Two strange men called me last night. They call themselves the Bogdanoff twins. I don’t know much about cryptocurrency- can you help them with their scheme?
category: Cryptography - 150
Investigations :
First, let’s have a look to the leaked_source.py file:
import hashlib
secret = ""
def generate_command_token(command, secret):
hashed = hashlib.sha1(secret+command).hexdigest()
return hashed
def validate_input(command, token_in):
token = hash_command(command, secret)
if token == token_in:
return True
else:
return False
while(True):
print("Command:")
command = raw_input(">>>")
print('Auth token:')
token = raw_input(">>>")
print
if validate_input(command, token) == False:
print("Error: Auth token does not match provided command..")
else:
execute_command(command)
print Well, we do not have the whole code but we can easily guess what we have to do.
When you see {SOME_HASHING_FUNC}(secret+command)
it’s about hash length extension attack and you can find some good information about it here
This attack consists in adding a payload in your entry so that when you calculate the new hash, you won’t have to know the secret. This attack would not work if it was SOME_HASHING_FUNC(command+secret).
Let’s now see this service using nc… we obtain this output:
$ nc bogged.wpictf.xyz 31337
BOGDANOFF:
Bonjour...
We have access to the Binance backdoor, and got you into a compromised teller station.
We need you to steal tethered cryptocurrency from people's wallets.
We were halted by an unfortunate countermeasure in the teller system, but we have an account ready to recieve the stolen crypto.
Steal the currency from cryptowojak123. Transfer it to not_b0gdan0ff.
Transfer everything... then we will kill him, and find another.
Do not fail us.
Welcome to the Binance Teller Terminal!
Please remember to use admin-issued auth tokens with each account transfer!
Either enter a command or one of the following keywords:
accounts: List of accounts currently on the system.
history: A history of prior terminal commands.
help: A reminder on how to use this terminal.
Command:
>>>help
You may either withdraw funds from an account or deposit funds to an account.
Withdraw with the following command:
withdraw ACCOUNT_NAME
Deposit with the following command:
deposit ACCOUNT_NAME
Commands may be chained, as follows:
withdraw ACCOUNT_NAME;deposit ACCOUNT_NAME;...
An authorization token unique to the command contents must exist for the transaction to succeed!
(Sorry, but we have to protect from malicious employees.)
Contact admin@dontactuallyemailthis.net to get auth tokens for different transfer commands!
Command:
>>>history
///// TRANSACTION HISTORY //////////////////////////
Command:
>>>withdraw john.doe
Auth token:
>>>b4c967e157fad98060ebbf24135bfdb5a73f14dc
Action successful!
Command:
>>>withdraw john.doe;deposit xXwaltonchaingangXx
Auth token:
>>>455705a6756fb014a4cba2aa0652779008e36878
Action successful!
Command:
>>>withdraw cryptowojak123;deposit xXwaltonchaingangXx
Auth token:
>>>e429ffbfe7cabd62bda3589576d8717aaf3f663f
Action successful!
Command:
>>>withdraw john.doe
Auth token:
>>>b4c967e157fad98060ebbf24135bfdb5a73f14dc
Action successful!
////////////////////////////////////////////////////
Command:
>>>So we have some transaction history and we want to transfer money from cryptowojak123 to not_b0gdan0ff.
We detect 1 interesting transaction fast and it will be useful later:
>>>withdraw cryptowojak123;deposit xXwaltonchaingangXx
Auth token:
>>>e429ffbfe7cabd62bda3589576d8717aaf3f663f
Action successful!Payload injection :
Now let’s work on payload injection.
There is a hash extender tool on github.
To inject a payload, we first need to know the secret length (I’ll injection only a ‘;’ for the moment) :
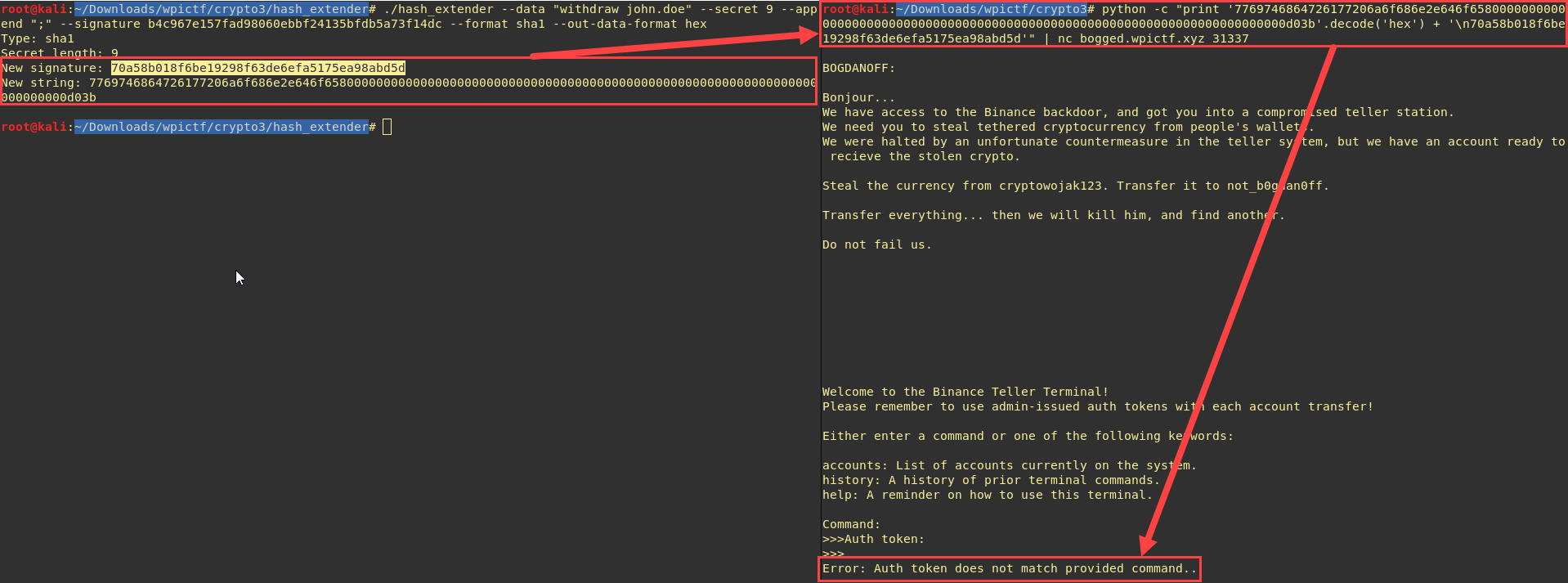
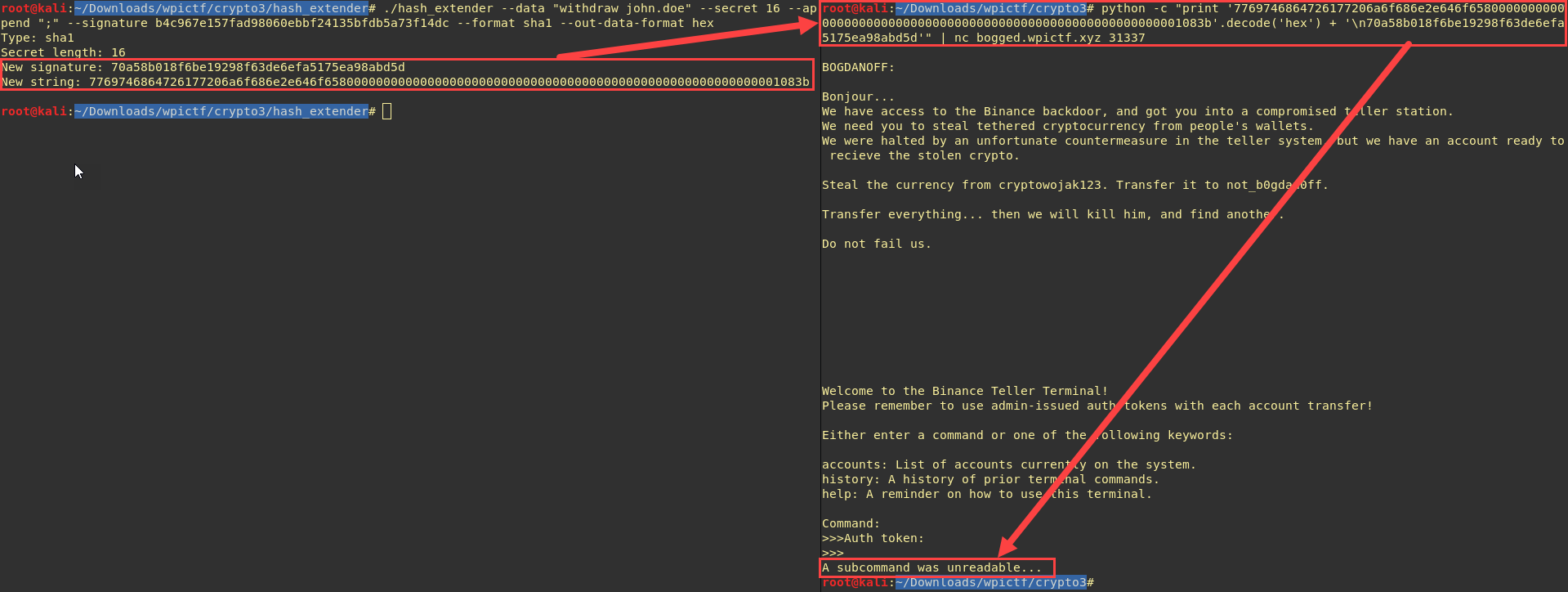
Great, our command is unreadable but our injection worked ! now let send something else than ‘;’, for example ‘;withdraw xXwaltonchaingangXx; deposit not_b0gdan0ff;’:
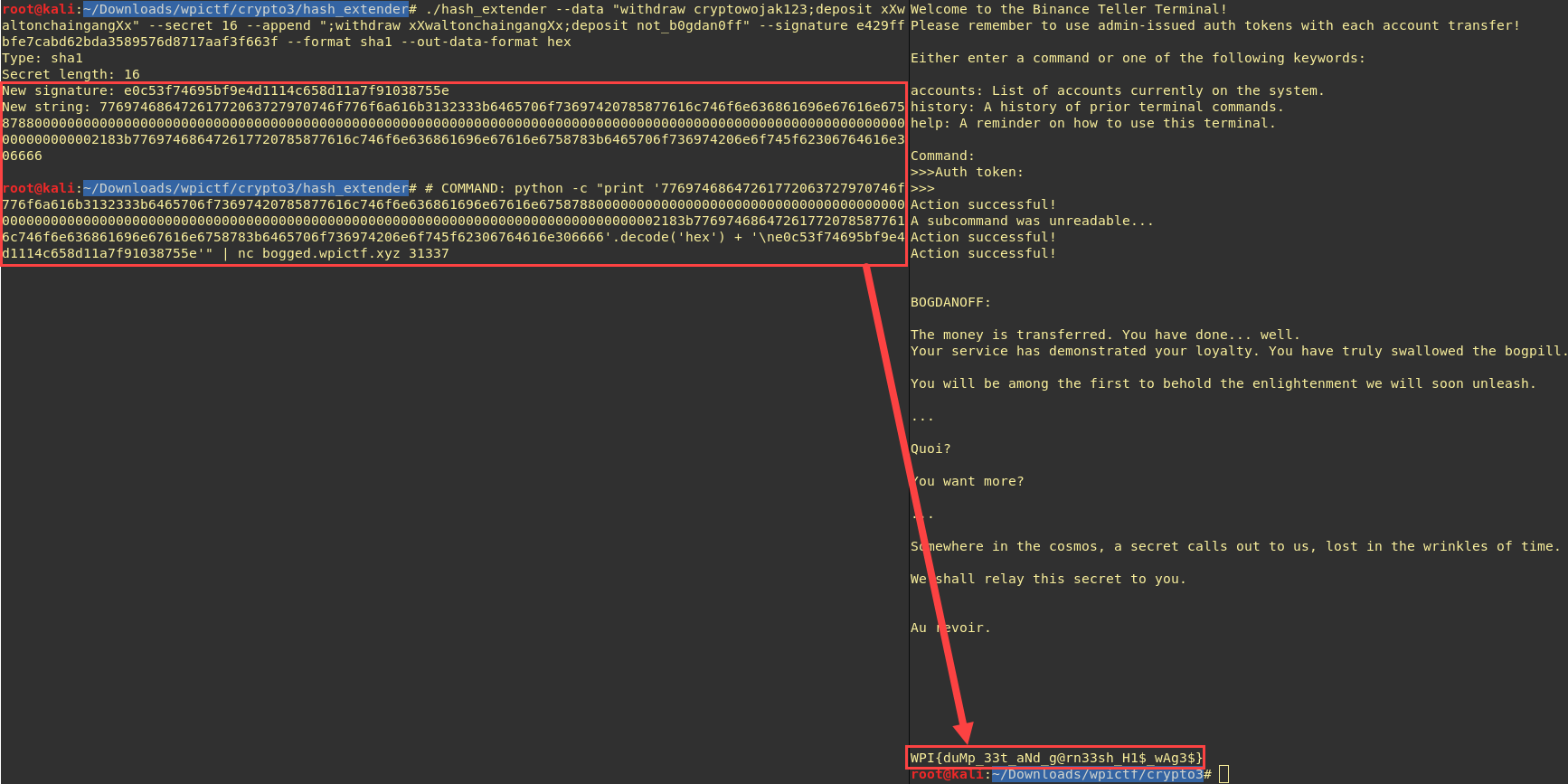
YEAH ! flag is : WPI{duMp_33t_aNd_g@rn33sh_H1$_wAg3$}
