ESGISECURITYDAY - Caper
06 Apr 2019description: Hey psst Petit, je t’ai entendu dans le bar. Tu cherches M0th3r ? oO Ne fais pas cette tète, faut vraiment que t’apprenne a être plus discret. J’écoute tout ce qui se passe à Cyber Build. D’ailleurs voici la capture d’une de ses dernières Opération. Ça vaut de l’OR.
category: Forensic
The challenge was providing a network traffic capture file : caper.pcapng. When we anlyse the first TCP session, we can see the following HTTP request: GET /config.json The content of the JSON file is show on the screenshot below:
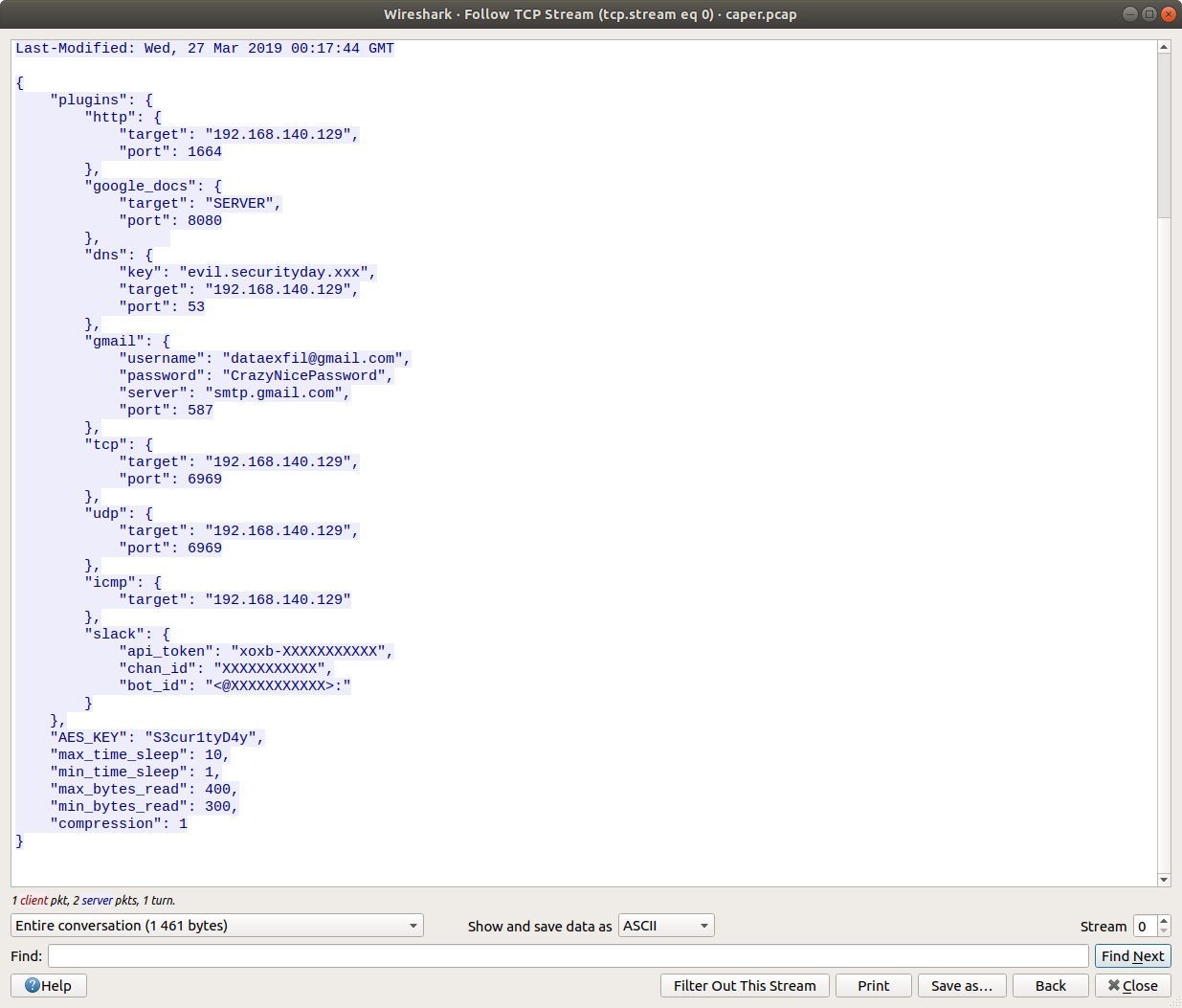
This file is a configuration file used by the tool DET (extensible) Data Exfiltration Toolkit.
Github : Data Exfiltration Toolkit
This tool gives the ability to exfiltrate files from a network by using multiple protocols and techniques. The file to exfiltrate is encrypted before beeing cut into pieces which are then sent base 64 encoded to the exfiltration server.
In our case 2 protocols were used for exfiltration : ICMP and HTTP.
And the key used for AES encryption : “S3cur1tyD4y”
Extract data from ICMP :
For this channel, the data is inserted into the Data field of ICMP request. We can use Tshark to gather the raw data inserted in the ICMP requests :
tshark -r caper.pcapng -Y "icmp.type==0" -T fields -e dataAfter converting the bytes into ASCII characters, we can decode the base64 and get some parts of the transaction :
I5LS9MX|!|flag.txt|!|REGISTER|!|3ec59ac658986a43921d824ae06ea494 I5LS9MX|!|1|!|d336c4194b8c3d5a8f96d50e926db9efdafa006037570e2899ddba564efd7ec5cacf0910d02ef8bbe51c40e97485e70f58737c1747dac16367c8feeb36ab6ad4325c949cfffbc81d6d2274abf75fd99ee7012f962ae71fca8e37f8df455305b4503824ff06cb1a4f31cd699308fcf03af16e59f4f07040fc6308eb8be9552766080b881fe595e40ca1ae05c9a0b0c5cfa371691ea4443643f825ed9676b3f21c73b49cf7b23b1b38269bfac263bfe4a6493425f0e6b4757a21552f73f7a58dc072f57fe73b6386326125b3fa93be68f185d523a95a3e48159a8244bee23ae70b3a4acf0fc917e94835a5e6f1bb0700f94472d924e1d4b89e57b46e64c5d47a00b4602ebad118ecdea48bb860691be4d8f7d9fccf0afcab660c6305193c84f91b8550ec7e354dafd8080ff01e4d29df192465a1da564237f583472d30886f0e9391bb6a0ddfbcfadda44b95ad069209a3e90b9bc3650831a3e63925b0adfe1161fcf4f28c8b26ebf147edfdfbfa73359c510fbb67b6b3c662ceed56cfac75ca8d06dc12df6e83efbbbfe2 I5LS9MX|!|2|!|4030de613bb59dc4329e59e6b9b857312522cf6a12dde919ac26a3bc96b62f98247ea32762fc0d85e19f9c33afee6925a00e8dc4865bff24b4931f7f9c4ad7039adc78009ba2ec11fb7c9485e864f3260e4e3c20ef6356e9f5636f6e28a55e09613782d167e10280c7aa83e568de30c9888c5c779fe6b9362118ba0e78e4b9a6bfee0305d173d7ce3e0670bd1a1c2cf1c2744e33ac1cd0fd97b323eb59a911023c28234c1af9224722809b1b3d51f2e10b7e90d804a5867394ab5ad4b64f3d170886f8f6078723a40bb1bd240f920a1b667de3638c1b48c0a2cec4c5674c1ae9825944fd62af5614aa3bdfc8758f6c74787a94bc29a7a336a78a02b49a31491f85c36ad714931bf5ca163c1e8dbb96fd6d7b87debc5ab5c5a3131d3e40f1ec659393c9e0ff6afdda92dd834fe1bd9d6e6942436242f070d044694c3fc230338f0ffcf77aefb98c2c12908789a45be681c7972198d3832ecc73cb563b4422d7461abc83a74785f4255b1801fba76da51991e5aba6e4a3cc99f90816ff00891ebd2da9693cb565fa66ba287cb6b1c39c I5LS9MX|!|4|!|DONE
We can see that we get the registration of the file with its filename and its hash, part 1 and part 2 of the data and the final message ending the transaction. We still miss part 0 and part 3 of the data in order to recover the original file.
Extract data from HTTP :
For this channel, the data is send over POST requests (application/x-www-form-urlencoded). Again, we use Tshark to extract the data from the PCAP :
tshark -r caper.pcapng -Y "http.request.method==POST" -T fields -e http.file_dataAfter decoding the base64 obtained with the previous command, we obtain the missing parts :
I5LS9MX|!|0|!|512b74ac48546bd6b065110d86c593658b15fee5c7f78f892e50442ef1aba6ec1e395c0cda4a6d475557212bca6bb2256dc1c0b6c8a0a10b3f45eefcfbb067efcd5b4317a8f8f4ee3a3d1566257aa6e1c15a5a5dafe9e400718843e65be2b97b47e8a17f501dffc81066f48f738a8b2b3c91c83a9038c44f4482c784747a5841a66fdf5b174be52f8df37313501a96ed1e5f7af7e0092db73a4eedd07f5522e82b19caee379a21f6eec66c8ef8488f6d85bc3b725c37d6fdb48b712e8d8cc2459eb18d6048f3cb44991016a66dcda1cf643bd600afd9addad340baee1e364a19a1fb5d03581e0d84b7cd3d2f0f5d97429a6cbdebf9a4c4f2342e830463066a0a0c149d95b8b478b603efe1c3b8af7f46cfd463c045bf5a906282615d0d87408e8db4677aeeb058bdb6da1999995a2b9231183464350bee1d6b37d947b5755dd9ee18cd8c20e0a3e65306d95dfe177290632fb74e2ab420a0de0771d64186c650bd20fb274dfe41f48098732f6f8b I5LS9MX|!|3|!|930776bb930de41985b536645e2b1b8bcd0b4107131480767667769f1181e03eadbc90eb65eaea01ba70ffdc54b9490275b6e8072b3143a264b10ab6e4a4ca50ca76ff35d6e4178a4c3c62a2049992863a88b6771f5c7a81a3a8c6d288f3740e8b8cb720ef38af92f73a683ef548f52943d89d89486603b3112d6d14d8fe4a2ff4e0e41e995976648d573d9a418ec60120aa30ffc3ac6f1d6f2b8138847fb357ce158789b6b912d4def3ffd5b7905c569f78b6a46d531d3f1c
Decrypt data and recover original file :
We first need to put back the different parts of the transaction in the right order.
We can then remove the first and last parts : I5LS9MX|!|flag.txt|!|REGISTER|!|3ec59ac658986a43921d824ae06ea494 and I5LS9MX|!|4|!|DONE.
We also remove the prefix : I5LS9MX|!|<id>|!| to keep only the AES encrypted data.
We can then write a script based on the source code of DET to decrypt the message :
#!/usr/bin/python
import hashlib
from Crypto.Cipher import AES
from zlib import compress, decompress
def aes_decrypt(message, key):
try:
# Retrieve CBC IV
iv = message[:AES.block_size]
message = message[AES.block_size:]
# Derive AES key from passphrase
aes = AES.new(hashlib.sha256(key).digest(), AES.MODE_CBC, iv)
message = aes.decrypt(message)
# Remove PKCS5 padding
unpad = lambda s: s[:-ord(s[len(s) - 1:])]
return unpad(message)
except Exception as i:
print i
return None
def retrieve_file(message, key):
content = aes_decrypt(message, key)
content = decompress(content)
print content
message="512b74ac48546bd6b065110d86c593658b15fee5c7f78f892e50442ef1aba6ec1e395c0cda4a6d475557212bca6bb2256dc1c0b6c8a0a10b3f45eefcfbb067efcd5b4317a8f8f4ee3a3d1566257aa6e1c15a5a5dafe9e400718843e65be2b97b47e8a17f501dffc81066f48f738a8b2b3c91c83a9038c44f4482c784747a5841a66fdf5b174be52f8df37313501a96ed1e5f7af7e0092db73a4eedd07f5522e82b19caee379a21f6eec66c8ef8488f6d85bc3b725c37d6fdb48b712e8d8cc2459eb18d6048f3cb44991016a66dcda1cf643bd600afd9addad340baee1e364a19a1fb5d03581e0d84b7cd3d2f0f5d97429a6cbdebf9a4c4f2342e830463066a0a0c149d95b8b478b603efe1c3b8af7f46cfd463c045bf5a906282615d0d87408e8db4677aeeb058bdb6da1999995a2b9231183464350bee1d6b37d947b5755dd9ee18cd8c20e0a3e65306d95dfe177290632fb74e2ab420a0de0771d64186c650bd20fb274dfe41f48098732f6f8bd336c4194b8c3d5a8f96d50e926db9efdafa006037570e2899ddba564efd7ec5cacf0910d02ef8bbe51c40e97485e70f58737c1747dac16367c8feeb36ab6ad4325c949cfffbc81d6d2274abf75fd99ee7012f962ae71fca8e37f8df455305b4503824ff06cb1a4f31cd699308fcf03af16e59f4f07040fc6308eb8be9552766080b881fe595e40ca1ae05c9a0b0c5cfa371691ea4443643f825ed9676b3f21c73b49cf7b23b1b38269bfac263bfe4a6493425f0e6b4757a21552f73f7a58dc072f57fe73b6386326125b3fa93be68f185d523a95a3e48159a8244bee23ae70b3a4acf0fc917e94835a5e6f1bb0700f94472d924e1d4b89e57b46e64c5d47a00b4602ebad118ecdea48bb860691be4d8f7d9fccf0afcab660c6305193c84f91b8550ec7e354dafd8080ff01e4d29df192465a1da564237f583472d30886f0e9391bb6a0ddfbcfadda44b95ad069209a3e90b9bc3650831a3e63925b0adfe1161fcf4f28c8b26ebf147edfdfbfa73359c510fbb67b6b3c662ceed56cfac75ca8d06dc12df6e83efbbbfe24030de613bb59dc4329e59e6b9b857312522cf6a12dde919ac26a3bc96b62f98247ea32762fc0d85e19f9c33afee6925a00e8dc4865bff24b4931f7f9c4ad7039adc78009ba2ec11fb7c9485e864f3260e4e3c20ef6356e9f5636f6e28a55e09613782d167e10280c7aa83e568de30c9888c5c779fe6b9362118ba0e78e4b9a6bfee0305d173d7ce3e0670bd1a1c2cf1c2744e33ac1cd0fd97b323eb59a911023c28234c1af9224722809b1b3d51f2e10b7e90d804a5867394ab5ad4b64f3d170886f8f6078723a40bb1bd240f920a1b667de3638c1b48c0a2cec4c5674c1ae9825944fd62af5614aa3bdfc8758f6c74787a94bc29a7a336a78a02b49a31491f85c36ad714931bf5ca163c1e8dbb96fd6d7b87debc5ab5c5a3131d3e40f1ec659393c9e0ff6afdda92dd834fe1bd9d6e6942436242f070d044694c3fc230338f0ffcf77aefb98c2c12908789a45be681c7972198d3832ecc73cb563b4422d7461abc83a74785f4255b1801fba76da51991e5aba6e4a3cc99f90816ff00891ebd2da9693cb565fa66ba287cb6b1c39c930776bb930de41985b536645e2b1b8bcd0b4107131480767667769f1181e03eadbc90eb65eaea01ba70ffdc54b9490275b6e8072b3143a264b10ab6e4a4ca50ca76ff35d6e4178a4c3c62a2049992863a88b6771f5c7a81a3a8c6d288f3740e8b8cb720ef38af92f73a683ef548f52943d89d89486603b3112d6d14d8fe4a2ff4e0e41e995976648d573d9a418ec60120aa30ffc3ac6f1d6f2b8138847fb357ce158789b6b912d4def3ffd5b7905c569f78b6a46d531d3f1c"
key="S3cur1tyD4y"
print retrieve_file(message.decode("hex"),key)After execution, this script gives us the flag : ESGI{DET_1s_A_R3aly_GR3aT_t00L} followed by a text in Latin…
